Fortinet
Persona-driven reporting
Data Visualization
FortiDevSec - Security Reporting
FortiDevSec - Security Reporting
FortiDevSec - Security Reporting
FortiDevSec - Security Reporting
FortiDevSec - Security Reporting
FortiDevSec - Security Reporting
This story is about how persona-based design revolutionized our security reporting feature in FortiDevSec.
This story is about how persona-based design revolutionized our security reporting feature in FortiDevSec.
This story is about how persona-based design revolutionized our security reporting feature in FortiDevSec.
This story is about how persona-based design revolutionized our security reporting feature in FortiDevSec.
This story is about how persona-based design revolutionized our security reporting feature in FortiDevSec.
This story is about how persona-based design revolutionized our security reporting feature in FortiDevSec.





July 2023 - Oct 2023
Timeline
UX Designer & Researcher
Role
July 2023 - Oct 2023
Timeline
UX Designer & Researcher
Role
Before we delve into the security reporting, let’s start
Before we delve into the security reporting, let’s start
What is FortiDevSec?
What is FortiDevSec?
FortiDevSec is like a security spell for your code! This static code analyzer scans your code automatically, finding and advising fixes vulnerabilities before they cause trouble.
FortiDevSec is like a security spell for your code! This static code analyzer scans your code automatically, finding and advising fixes vulnerabilities before they cause trouble.
1
Code Scanning
1
Code Scanning
1
Code Scanning
1
Code Scanning
1
Code Scanning
2
Data Aggregation
2
Data Aggregation
2
Data Aggregation
2
Data Aggregation
2
Data Aggregation
3
Actionable Responses
3
Actionable Responses
3
Actionable Responses
3
Actionable Responses
3
Actionable Responses
Problem space
Problem space
From Data Deluge to Insights
From Data Deluge to Insights
FortiDevSec is like a security spell for your code! This static code analyzer scans your code automatically, finding and advising fixes vulnerabilities before they cause trouble.
FortiDevSec is like a security spell for your code! This static code analyzer scans your code automatically, finding and advising fixes vulnerabilities before they cause trouble.

1
Information overload
FortiDevSec scanning raw results was overwhelming and was making it difficult to identify and prioritise issues for different personas.
1
Information overload
FortiDevSec scanning raw results was overwhelming and was making it difficult to identify and prioritise issues for different personas.
1
Information overload
FortiDevSec scanning raw results was overwhelming and was making it difficult to identify and prioritise issues for different personas.
1
Information overload
FortiDevSec scanning raw results was overwhelming and was making it difficult to identify and prioritise issues for different personas.
1
Information overload
FortiDevSec scanning raw results was overwhelming and was making it difficult to identify and prioritise issues for different personas.

2
Missing the bigger picture
Lack of historical trends and comparative analysis obscured application performance and progress over time, making it difficult for stakeholders to understand security posture and make informed decisions.
2
Missing the bigger picture
Lack of historical trends and comparative analysis obscured application performance and progress over time, making it difficult for stakeholders to understand security posture and make informed decisions.
2
Missing the bigger picture
Lack of historical trends and comparative analysis obscured application performance and progress over time, making it difficult for stakeholders to understand security posture and make informed decisions.
2
Missing the bigger picture
Lack of historical trends and comparative analysis obscured application performance and progress over time, making it difficult for stakeholders to understand security posture and make informed decisions.
2
Missing the bigger picture
Lack of historical trends and comparative analysis obscured application performance and progress over time, making it difficult for stakeholders to understand security posture and make informed decisions.
“Numbers have an important story to tell. They rely on you to give them a clear and convincing voice. ― Stephen Few”
Impact
Impact
Empowered Users, Enhanced Security
Empowered Users, Enhanced Security
1
Reduced information overload
Introduced targeted data visualisation and personalized views.
1
Reduced information overload
Introduced targeted data visualisation and personalized views.
1
Reduced information overload
Introduced targeted data visualisation and personalized views.
1
Reduced information overload
Introduced targeted data visualisation and personalized views.
1
Reduced information overload
Introduced targeted data visualisation and personalized views.
2
Slashed search time by 2X with efficient filters
Offered a customizable, in-workflow filter view, preferred by developers. Reported spending half time searching for vulnerabilities.
2
Slashed search time by 2X with efficient filters
Offered a customizable, in-workflow filter view, preferred by developers. Reported spending half time searching for vulnerabilities.
2
Slashed search time by 2X with efficient filters
Offered a customizable, in-workflow filter view, preferred by developers. Reported spending half time searching for vulnerabilities.
2
Slashed search time by 2X with efficient filters
Offered a customizable, in-workflow filter view, preferred by developers. Reported spending half time searching for vulnerabilities.
2
Slashed search time by 2X with efficient filters
Offered a customizable, in-workflow filter view, preferred by developers. Reported spending half time searching for vulnerabilities.
3
Increased actionable insights by 50%
Actionable data points have been added to be consumed by each persona type.
3
Increased actionable insights by 50%
Actionable data points have been added to be consumed by each persona type.
3
Increased actionable insights by 50%
Actionable data points have been added to be consumed by each persona type.
3
Increased actionable insights by 50%
Actionable data points have been added to be consumed by each persona type.
3
Increased actionable insights by 50%
Actionable data points have been added to be consumed by each persona type.
Developer level
Goal:
Access detailed vulnerability information with powerful filtering (app, severity, type, etc.) and the ability to save filter presets.
Name: Cha eun-koo
Position: Senior software engineer
Product: Sodo IDE, Sodo Chrome plugin
Goal:
Access detailed vulnerability information with powerful filtering (app, severity, type, etc.) and the ability to save filter presets.
Name: Cha eun-koo
Position: Senior software engineer
Product: Sodo IDE, Sodo Chrome plugin
Organization level
Organization level
Goal:
Goal: Organization level real-time actionable insights & historical trends
Name: Rachel Chen
Position: Chief Information Security Officer (CISO)
Organnization: CloudTree
Goal:
Goal: Organization level real-time actionable insights & historical trends
Name: Rachel Chen
Position: Chief Information Security Officer (CISO)
Organnization: CloudTree
Goal:
Goal: Organization level real-time actionable insights & historical trends
Name: Rachel Chen
Position: Chief Information Security Officer (CISO)
Organnization: CloudTree
Goal:
Goal: Organization level real-time actionable insights & historical trends
Name: Rachel Chen
Position: Chief Information Security Officer (CISO)
Organnization: CloudTree
Goal:
Goal: Organization level real-time actionable insights & historical trends
Name: Rachel Chen
Position: Chief Information Security Officer (CISO)
Organnization: CloudTree
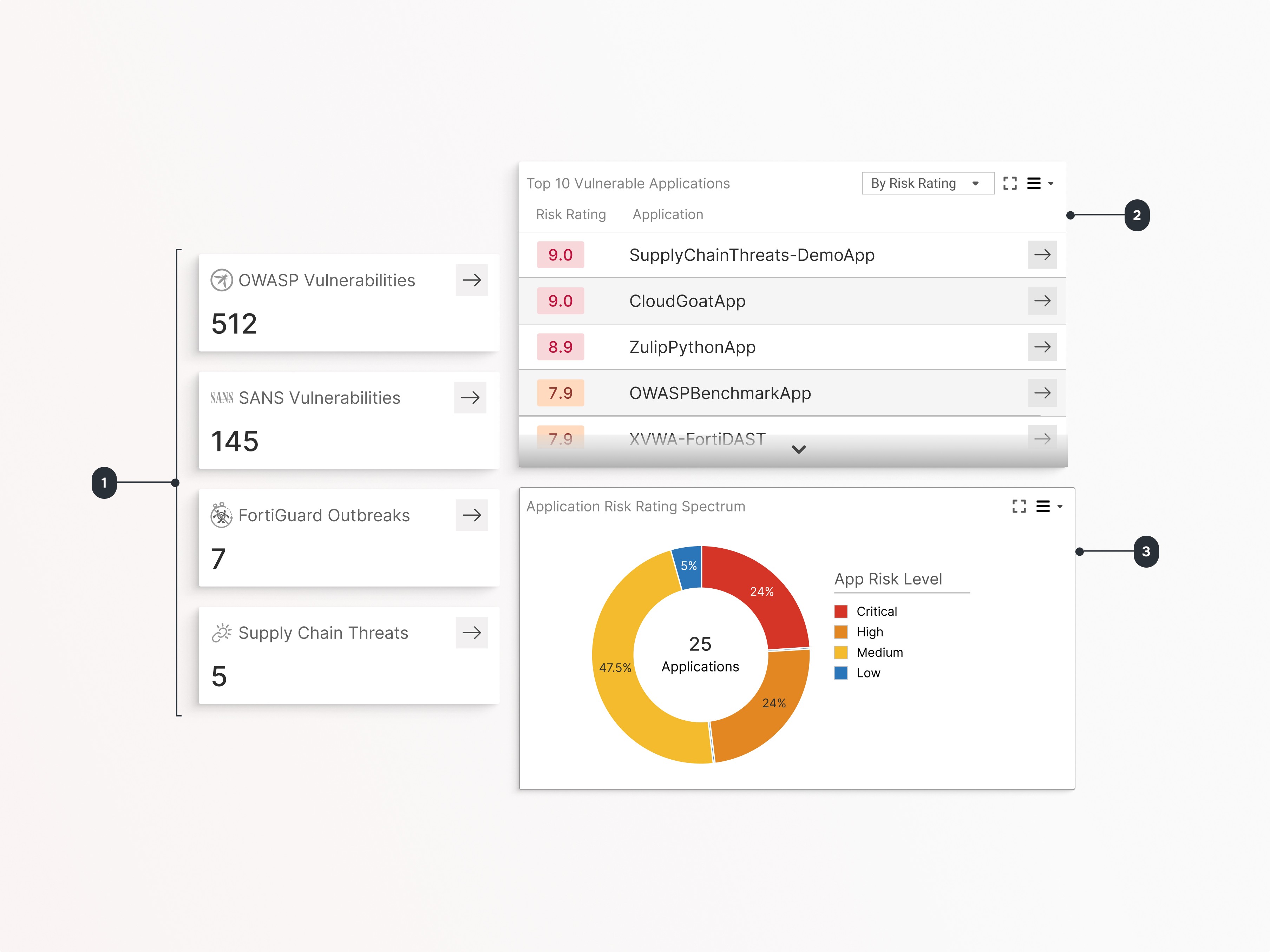
1
Threat Radar
Quickly identify the biggest threats volume such as OWASP, SANS 25 vulnerabilities, FortiOutbreak alerts, and supply chain threats.
1
Threat Radar
Quickly identify the biggest threats volume such as OWASP, SANS 25 vulnerabilities, FortiOutbreak alerts, and supply chain threats.
1
Threat Radar
Quickly identify the biggest threats volume such as OWASP, SANS 25 vulnerabilities, FortiOutbreak alerts, and supply chain threats.
1
Threat Radar
Quickly identify the biggest threats volume such as OWASP, SANS 25 vulnerabilities, FortiOutbreak alerts, and supply chain threats.
1
Threat Radar
Quickly identify the biggest threats volume such as OWASP, SANS 25 vulnerabilities, FortiOutbreak alerts, and supply chain threats.
2
Focus on Top 10 Vulnerable Applications
See list of your most vulnerable applications.
2
Focus on Top 10 Vulnerable Applications
See list of your most vulnerable applications.
2
Focus on Top 10 Vulnerable Applications
See list of your most vulnerable applications.
2
Focus on Top 10 Vulnerable Applications
See list of your most vulnerable applications.
2
Focus on Top 10 Vulnerable Applications
See list of your most vulnerable applications.
3
Visualise Risk Distribution
Your overall risk posture with a pie chart that shows the distribution of applications by risk level (Critical, High, Medium, Low).
3
Visualise Risk Distribution
Your overall risk posture with a pie chart that shows the distribution of applications by risk level (Critical, High, Medium, Low).
3
Visualise Risk Distribution
Your overall risk posture with a pie chart that shows the distribution of applications by risk level (Critical, High, Medium, Low).
3
Visualise Risk Distribution
Your overall risk posture with a pie chart that shows the distribution of applications by risk level (Critical, High, Medium, Low).
3
Visualise Risk Distribution
Your overall risk posture with a pie chart that shows the distribution of applications by risk level (Critical, High, Medium, Low).
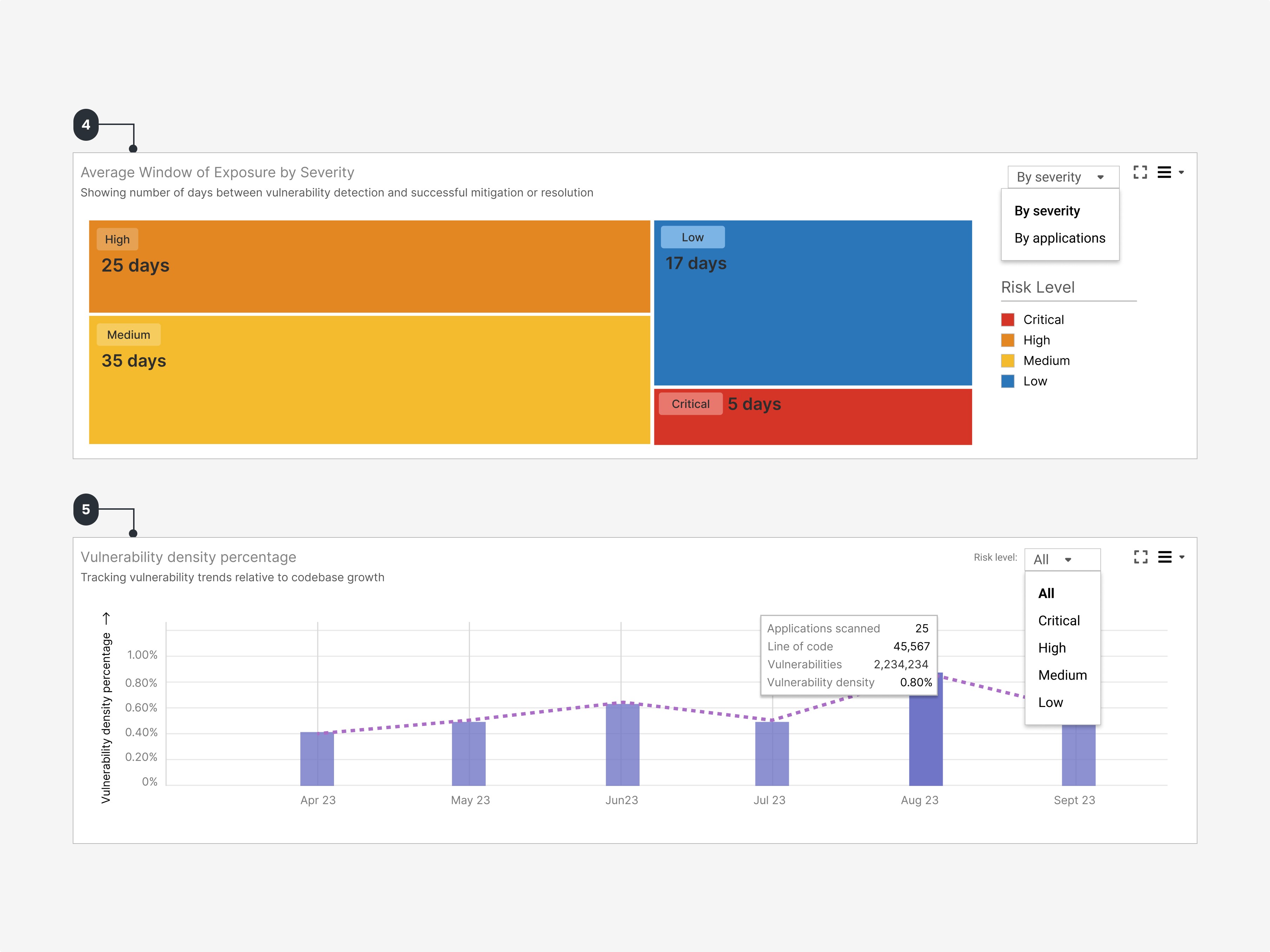
4
Exposure Window
Treemap visualization to take action on ageing vulnerabilities.
4
Exposure Window
Treemap visualization to take action on ageing vulnerabilities.
4
Exposure Window
Treemap visualization to take action on ageing vulnerabilities.
4
Exposure Window
Treemap visualization to take action on ageing vulnerabilities.
4
Exposure Window
Treemap visualization to take action on ageing vulnerabilities.
5
Vulnerability Density
See how your overall vulnerability landscape is evolving.
5
Vulnerability Density
See how your overall vulnerability landscape is evolving.
5
Vulnerability Density
See how your overall vulnerability landscape is evolving.
5
Vulnerability Density
See how your overall vulnerability landscape is evolving.
5
Vulnerability Density
See how your overall vulnerability landscape is evolving.
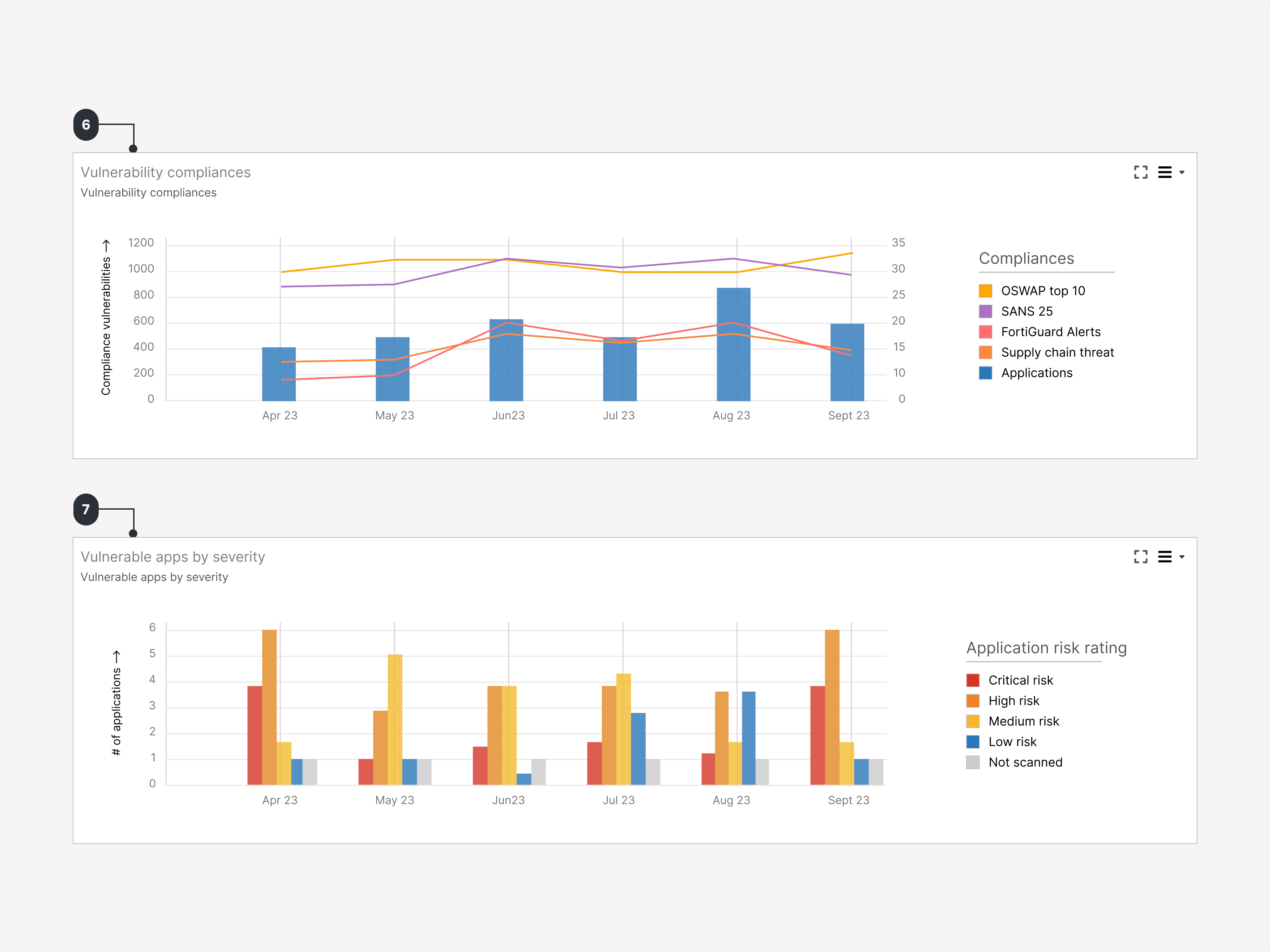
6
Compliance Posture Overview
This widget shows the number of applications scanned and their compliance with key security standards over time.
6
Compliance Posture Overview
This widget shows the number of applications scanned and their compliance with key security standards over time.
6
Compliance Posture Overview
This widget shows the number of applications scanned and their compliance with key security standards over time.
6
Compliance Posture Overview
This widget shows the number of applications scanned and their compliance with key security standards over time.
6
Compliance Posture Overview
This widget shows the number of applications scanned and their compliance with key security standards over time.
7
Vulnerable Applications
Showing the trend of vulnerable applications by severity over time period selected.
7
Vulnerable Applications
Showing the trend of vulnerable applications by severity over time period selected.
7
Vulnerable Applications
Showing the trend of vulnerable applications by severity over time period selected.
7
Vulnerable Applications
Showing the trend of vulnerable applications by severity over time period selected.
7
Vulnerable Applications
Showing the trend of vulnerable applications by severity over time period selected.
Application level
Application level
Goal:
View an actionable overview of current security metrics and insights into the security trend of my application.
Name: Vijay Reddy
Position: Technical Manager
Product: Sodo IDE
Goal:
View an actionable overview of current security metrics and insights into the security trend of my application.
Name: Vijay Reddy
Position: Technical Manager
Product: Sodo IDE
Goal:
View an actionable overview of current security metrics and insights into the security trend of my application.
Name: Vijay Reddy
Position: Technical Manager
Product: Sodo IDE
Goal:
View an actionable overview of current security metrics and insights into the security trend of my application.
Name: Vijay Reddy
Position: Technical Manager
Product: Sodo IDE
Goal:
View an actionable overview of current security metrics and insights into the security trend of my application.
Name: Vijay Reddy
Position: Technical Manager
Product: Sodo IDE
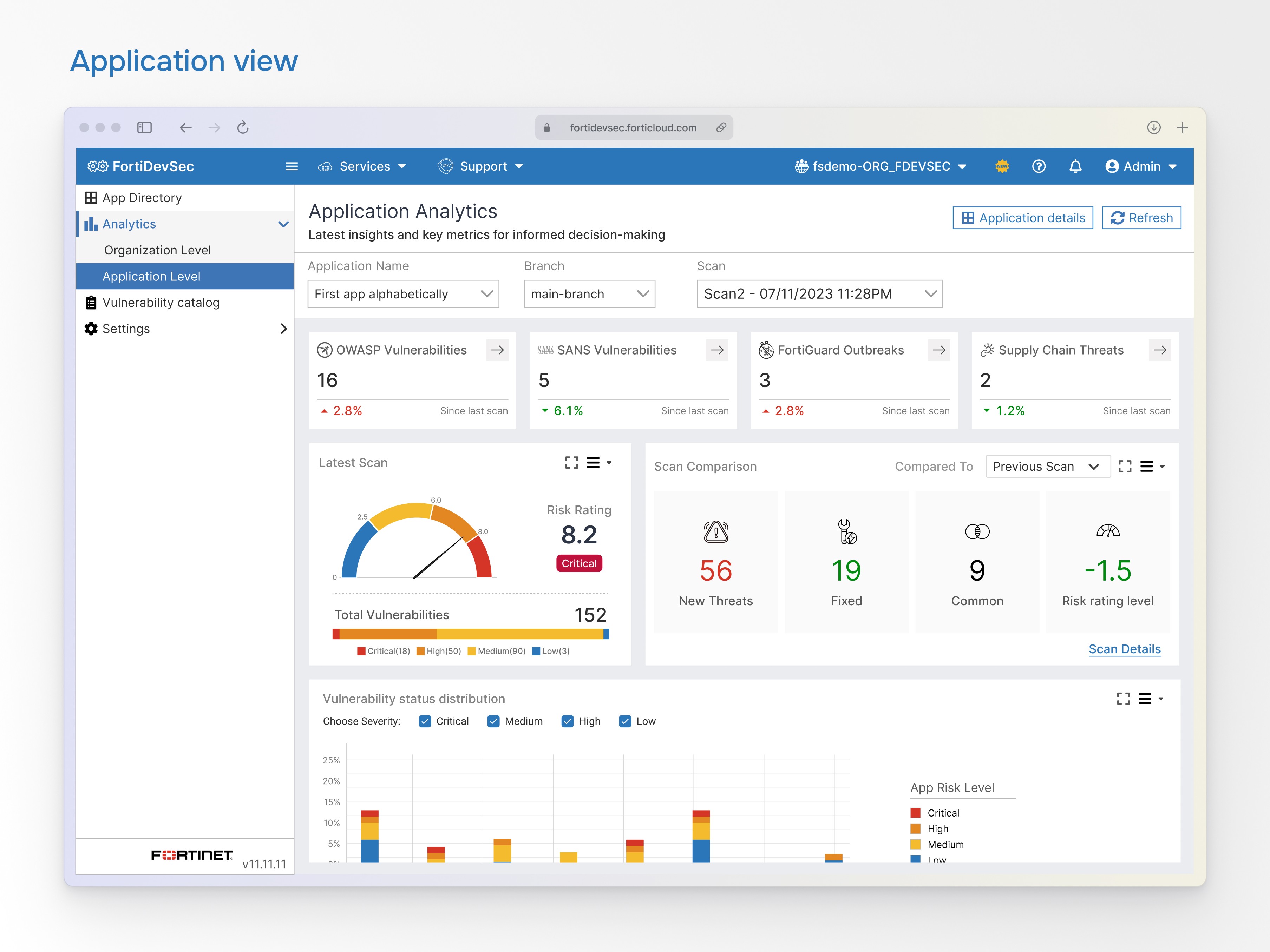
Application view
Widgets from application view
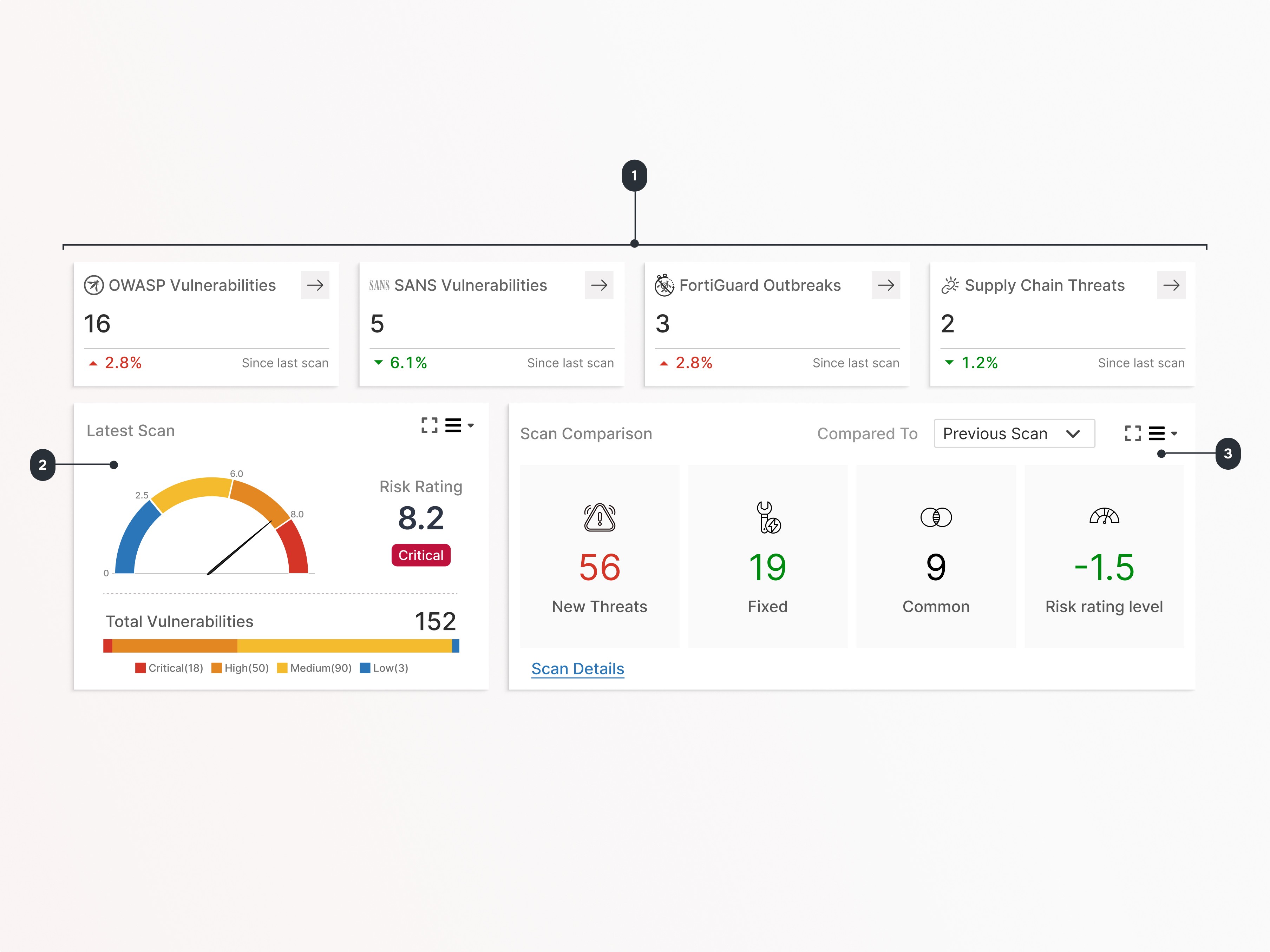
1
Threat Radar
This widget displays the number of threats detected across OWASP, SANS, FortiGuard, and Supply Chain categories, comparing the latest scan results with the previous ones.
1
Threat Radar
This widget displays the number of threats detected across OWASP, SANS, FortiGuard, and Supply Chain categories, comparing the latest scan results with the previous ones.
1
Threat Radar
This widget displays the number of threats detected across OWASP, SANS, FortiGuard, and Supply Chain categories, comparing the latest scan results with the previous ones.
1
Threat Radar
This widget displays the number of threats detected across OWASP, SANS, FortiGuard, and Supply Chain categories, comparing the latest scan results with the previous ones.
1
Threat Radar
This widget displays the number of threats detected across OWASP, SANS, FortiGuard, and Supply Chain categories, comparing the latest scan results with the previous ones.
2
Application Risk Snapshot
Get application risk rating score with the distribution of vulnerabilities by severity.
2
Application Risk Snapshot
Get application risk rating score with the distribution of vulnerabilities by severity.
2
Application Risk Snapshot
Get application risk rating score with the distribution of vulnerabilities by severity.
2
Application Risk Snapshot
Get application risk rating score with the distribution of vulnerabilities by severity.
2
Application Risk Snapshot
Get application risk rating score with the distribution of vulnerabilities by severity.
3
Scan Comparison
Compare your latest scan (default: previous) to identify new threats, resolved issues, common vulnerabilities, and changes in the overall risk score.
3
Scan Comparison
Compare your latest scan (default: previous) to identify new threats, resolved issues, common vulnerabilities, and changes in the overall risk score.
3
Scan Comparison
Compare your latest scan (default: previous) to identify new threats, resolved issues, common vulnerabilities, and changes in the overall risk score.
3
Scan Comparison
Compare your latest scan (default: previous) to identify new threats, resolved issues, common vulnerabilities, and changes in the overall risk score.
3
Scan Comparison
Compare your latest scan (default: previous) to identify new threats, resolved issues, common vulnerabilities, and changes in the overall risk score.
1
Interesting finding
Interesting finding
Interesting finding
In the journey of refining our security dashboard, a pivotal moment arose when I engaged with application owners. A common thread emerged - a desire for a quick, comparative insight into their application's security standing.
Developer level
Developer level
Goal:
Access detailed vulnerability information with powerful filtering (app, severity, type, etc.) and the ability to save filter presets.
Name: Cha eun-koo
Position: Senior software engineer
Product: Sodo IDE, Sodo Chrome plugin
Goal:
Access detailed vulnerability information with powerful filtering (app, severity, type, etc.) and the ability to save filter presets.
Name: Cha eun-koo
Position: Senior software engineer
Product: Sodo IDE, Sodo Chrome plugin
Goal:
Access detailed vulnerability information with powerful filtering (app, severity, type, etc.) and the ability to save filter presets.
Name: Cha eun-koo
Position: Senior software engineer
Product: Sodo IDE, Sodo Chrome plugin
Goal:
Access detailed vulnerability information with powerful filtering (app, severity, type, etc.) and the ability to save filter presets.
Name: Cha eun-koo
Position: Senior software engineer
Product: Sodo IDE, Sodo Chrome plugin
Goal:
Access detailed vulnerability information with powerful filtering (app, severity, type, etc.) and the ability to save filter presets.
Name: Cha eun-koo
Position: Senior software engineer
Product: Sodo IDE, Sodo Chrome plugin
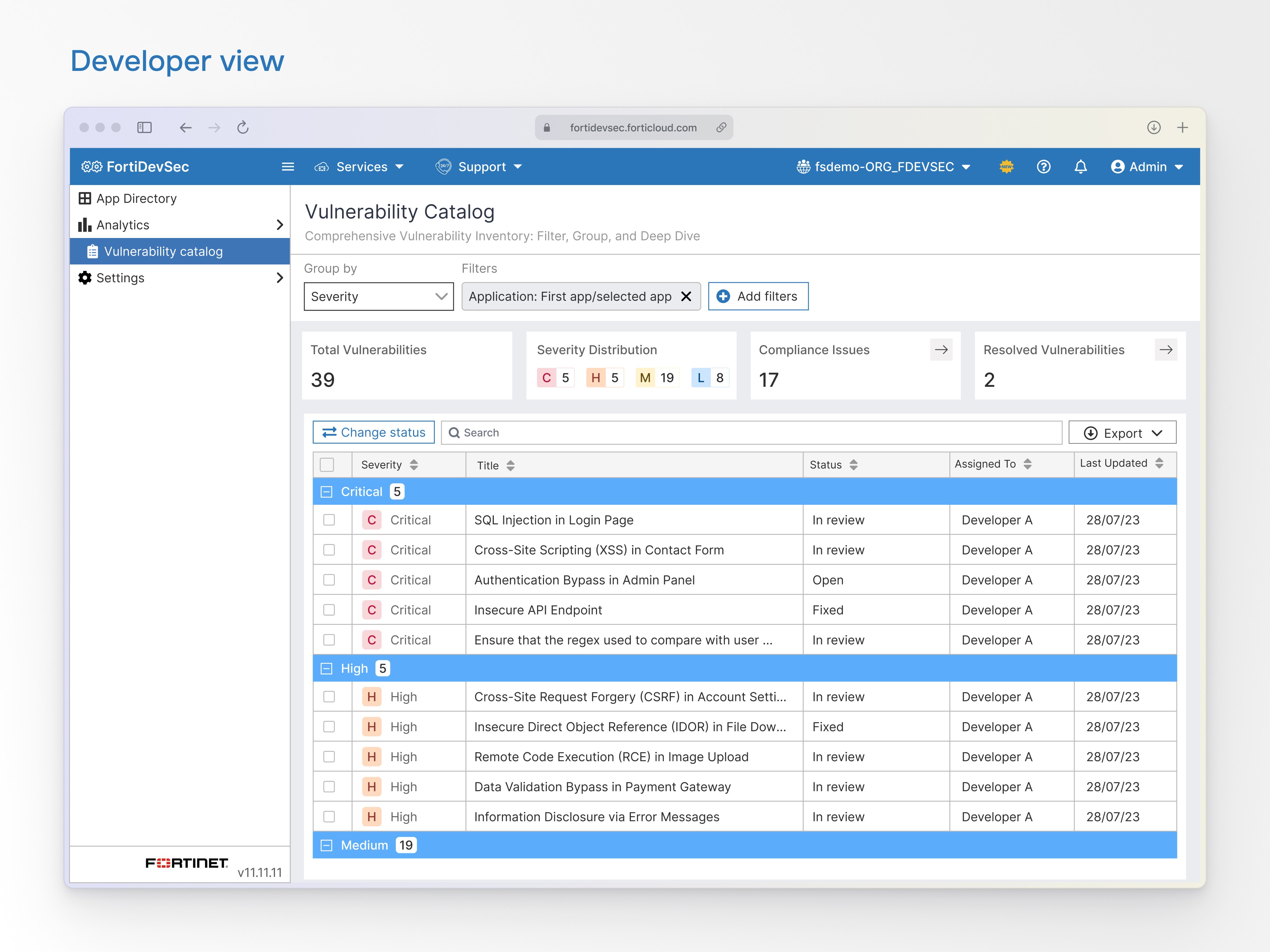
This view shows total vulnerabilities, severity distribution, compliance issues, resolved vulnerabilities, and offers flexible export options for developers.
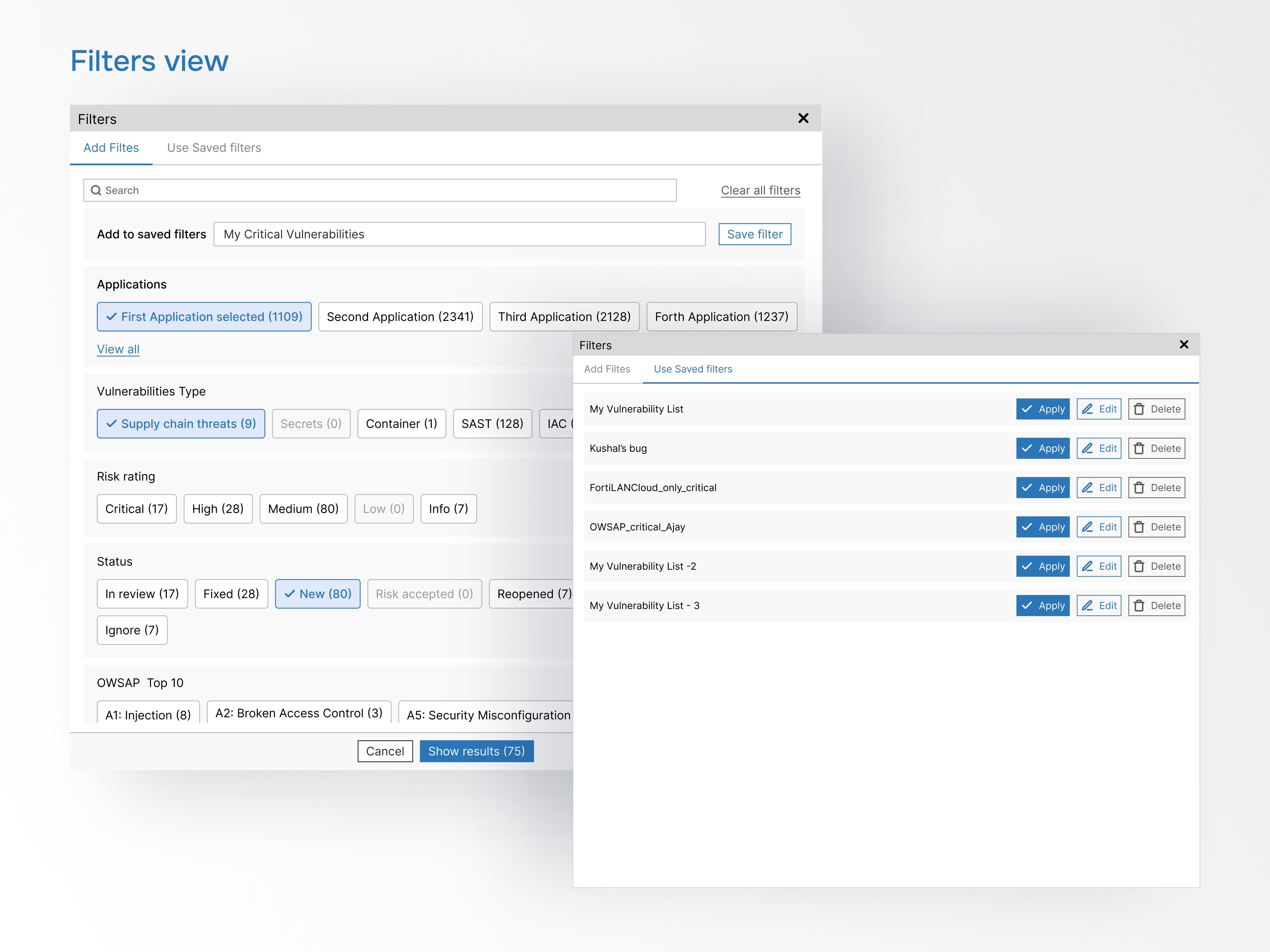
Reusable filter presets to save developers time and advanced filtering options by application, severity, type, and vulnerability age.
🎬Behind the Design
🎬Behind the Design
See how I explored user needs, iterated on solutions, and landed on the final design.
See how I explored user needs, iterated on solutions, and landed on the final design.
See how I explored user needs, iterated on solutions, and landed on the final design.
See how I explored user needs, iterated on solutions, and landed on the final design.
See how I explored user needs, iterated on solutions, and landed on the final design.
Conclusion
Dashboards are not suitable for every persona. Developers preferred a simple, flexible, and filterable view where vulnerability details were clear.
Adopting a phased delivery approach proved more effective for better user adoption.